A supply chain is defined as a network between a company and its suppliers to produce and distribute a specific product or service to a list of final buyers. This network includes different activities, involving various people and entities, information, and resources. In today’s world, every aspect of the world especially business is exposed to technology; more specifically the supply chain owners and participants need to make sure that not only their companies are secure from cyber-attacks, but the rest of the affiliates of the supply chain are secured as well. This need becomes more prominent with the rise in popularity of ransomware attacks, which are not just yet another type of malware, but it is a criminal business model, in which the perpetrator seeks to obtain benefits by taking hostage a victim’s data, infrastructure, economic output, intellectual property, or even privacy. To put this trend in perspective, companies, and organizations of all sizes around the world, from SMEs, mid-sized and multinationals to the public sector and governments, faced a 148% increase in 2021 by ransomware hits.
Regarding supply chains in particular, the perpetrators are targeting essential goods and services (there are examples from the health and safety, oil and gas sector etc.), because the criticality and effect on daily life increases the urgency for resolution and makes the chance of ransom payment much more likely and immediate. The cases we see are increasing in success, and as more attacks gain the attention of the media, hackers are realizing that they can extort companies with a large customer base to maximize the impact of their attacks. This, paired with the scale of many organizations’ vendor ecosystems, poses an enormous emphasis on preventing supply chain attacks through third-party Risk management.
Steps to shielding against ransomware attacks
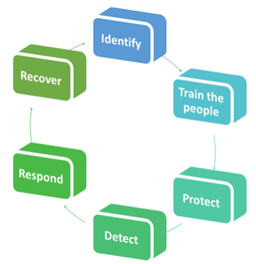
In order for companies to be prepared for ransomware attacks, the National Institute of Standards and Technology (NIST) cybersecurity framework proposes 6 steps that should be considered for increased preparedness:
- Protect
- Detect
- Respond
- Recover
- Identify
- Train the people
The latest critical addition is the 6th step since it is well known that people are often the critical point of failure in the cyber security process of a company.
In conclusion, in a supply chain scenario, these steps and any prevention and mitigation measures should be followed by all entities in the supply chain and this has been further exacerbated since COVID-19 accelerated digital business and the trend wherein several digital assets and individuals are located outside the traditional enterprise infrastructure. To avoid ransomware attacks:
- all entities of the supply chain and most importantly the people working in them need to be vigilant. They need to be aware of what ransomware is, what the implications are and to be on the lookout for any signs.
- Train the employees to be able to detect phishing attempts (the main way to start a ransomware attack) and have a strong reporting process towards the security team.
- Simulate, plan and share; simulating an attack and planning on how to respond can be critical for recovering. Sharing any findings with employees and partners can help strengthen the whole chain instead of just one link of the supply chain.
So what do you think? What do you do, to train the people in your organization to recognize mostly phishing attempts? And if you are not working in security how often have you been tested to click on a link or open a file that looked (or not) suspicious for training purposes?

This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.