The only perfectly secure system is one that does not communicate with any others.
The overall level of security of any ecosystem is equal to that of its most vulnerable component.
In the present times of the COVID-19 pandemic outbreak, the world was forced to come to terms and exercise techniques and tactics that were till recently explicitly known in their application in security-related fields.
The fundamental concept of mitigating the risk of contamination by blocking any sort of interaction and communication between entities was the first point of action that was taken against COVID-19 worldwide, which entailed boxing in populations in villages, cities, countries, alas, to no result.
The security measures that were then enforced, like the mandatory wearing of masks, revealed the validity of the fact that if the whole of a population does not practice the same high level of protection, it remains as vulnerable as their least protected individual members. The collective use of a mask does not protect each member individually but rather the other way around: It is the holistic protection measures when practised by all that ensure a population’s security as a whole and subsequently that of each individual member.
This will become similarly evident even after a vaccine will be discovered as to issues pertaining to ensure the global availability of vaccination for the whole of the population.
All the above depict the similarities between the human ecosystems and cyber range environments as far as the similar application of these fundamental rules is concerned, that are indeed applicable for both. Of course, the application of isolation for any cyber system is an oxymoron since the core of their existence evolves around the exchange of data.
As far as the second rule is concerned though, this is not the case. The diversity of cyber systems and their human assets (users) demand a holistic approach when aiming to strengthen security. For example, a professional office environment with employees ranging from IT security experts to secretarial staff, with basic security knowledge at best, call for a customized and tailored security training adapted to the various levels and needs of the employees.
The range and diversity of these requirements demand a versatile training platform that can adequately facilitate distinct needs that range from
- simple training courses aimed at educating secretarial staff about common cyber risks (social engineering attacks, spyware etc.) using user-friendly techniques like card games, interactive content, quizzes
up to
- complex hands-on security expert training, consisting of various emulated environments, simulated components as parts of complex scenarios (Multi-User Red/Blue Teams, Capture the Flag etc.)
Aiming to address these diverse needs, the THREAT-ARREST project aspires to design, build, and evaluate an advanced security training framework and platform, incorporating emulation, simulation, serious gaming and visualization capabilities. Training is aligned with operational cyber-system security assurance mechanisms to ensure its relevance.
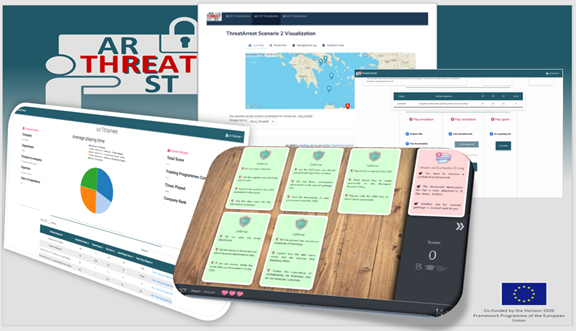
ITML, in the context of the project, is developing the Training Tool; the main functionalities of which include:
- User authentication and management, as well as an enhanced user interface for all Trainers and Trainees, providing them detailed information about the available courses, related study documentation and access to all the rest of the platform modalities
- Translating the training preparation (CTTP) models into a complete cyber range environment by instantiating and configuring all participating modalities (Virtual Machines, Emulated Components, Gaming Courses etc.)
- Performing elaborate Programme and trainee evaluation using an extended pool of recorded metrics to perform statistical analysis of the trainees’ performance. These metrics include detailed tracking and scoring of the trainees’ actions and response times in the cyber range environment, their use of help content (hints), etc.
The first version of the THREAT-ARREST platform has been completed and after having successfully undergone its pilot testing phase, it is now under development to deliver the final version of functionalities and features. THREAT-ARREST will be then tested by a number of end-users including pilots, to ensure the platform’s sustainability and its usefulness for future application in real-world environment.

THREAT-ARREST project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 786890.

The contents of this publication do not necessarily reflect the opinion of the European Union. The article reflects only the author’s view and the sole responsibility of this publication lies with the author. The Research Executive Agency (REA) is not responsible for any use that may be made of the information contained therein.
