Ransomware is not just yet another type of malware, it is a criminal business model in which the perpetrator seeks to obtain benefit by taking hostage of a victim’s data, infrastructure, economic output, intellectual property, or even privacy.

Companies and organizations of all sizes around the world, from SMEs, mid-sized and multinationals to the public sector and governments are facing a 148% increase in 2021 by ransomware hits1. Therefore, this growing threat of ransomware attacks has generated a significant increase in all quarters compared to 2020.
There is no exception: all industries are affected as reported: from the retail industry, maritime, technology, petroleum, tourism, healthcare and education.
How to prevent ransomware attacks?
Below are 6 complementary steps that should be considered by organizations wanting to prepare for and limit the impact of Ransomware, as suggested by the NIST Cyber Security Framework[1], with a critical addition: onboarding and training the people!
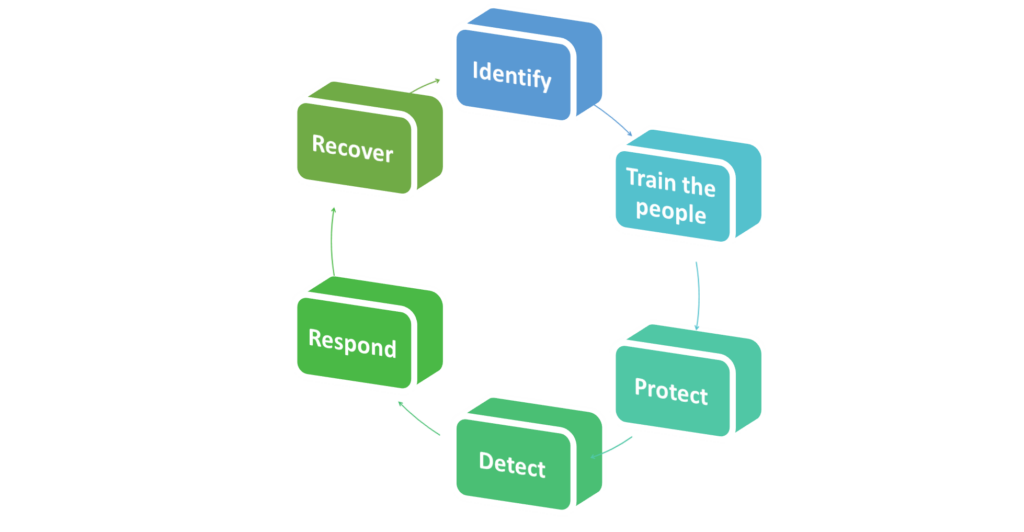
The following video presents the NIST Cybersecurity Security Framework.
What do Business Leaders think are the Top Security Priorities?
According to Gartner[2], there are some Key Findings that business leaders must pay attention to:
- Increasingly sophisticated ransomware attacks are specifically targeting backup data and administrator functions.
- No single solution can completely protect an organization from ransomware attacks.
- The threat from increasingly sophisticated ransomware is growing, with attacks being launched by criminal and governmental organizations worldwide.
- Ransomware is frequently deployed as a component of a broader attack that looks to compromise critical systems and administrative functions.
All the aspects stress the need for early identification of any cybersecurity-related incident: with ransomware being one of the most impactful. Preventing ransomware attacks in the first place can save your business tens of thousands of dollars -or perhaps millions – in losses due to interrupted operations, data loss, and other consequences.
Is your Company Prepared?
There are a number of steps that companies can take to reduce the risk of a ransomware attack, as well as the risk of damage to data and/or reputation if an attack occurs. These include:
- Eliminate network sharing protocols — Avoid the use of simple network sharing protocols, such as CIFS or NFS when implementing storage for backup data.
- Protect the backup system — Protection of both the backup administration console and copies of backup data ensures usable backups are always available.
- Use multifactor authentication for administrative accounts — Implement two-factor authentication for all backup administrator accounts and ensure that accounts are configured with the minimum privilege required to function.
- Create an isolated recovery environment — Make ransomware recovery via an IRE part of your disaster recovery plan and include it in future disaster recovery tests.
Backups are critical: Even if your company is prepared to protect, detect and respond, have you tried to recover from your backup files? How long did it take, and could you selectively restore parts of your infrastructure?
How Should a Company Respond to Ransomware?
So, you’ve been attacked by ransomware. Cyber-criminals are constantly evolving their attack methods and strategies. These cyber-criminals will exploit any weaknesses they can find to make a profit from your business’ hard work. By taking these initial steps the attack’s effectiveness could be reduced:
- Identify the attack: Tracing the root cause is the first step to respond when hit by ransomware. Inspecting system-level events, files and other evidence on the endpoint (computer, server, laptop or another networked device), and use of proper tools will help define the root cause or weak spot that led to being hit by ransomware. This is no trivial task and highly skilled security experts are required to perform the mentioned forensics investigation.
- Isolate the issue and stop expansion: Separation of the infected resources must take place as soon as possible. This obvious action highlights the necessity to identify fast and act faster.
- Select the best recovery plan: It might be restore from a full backup, a clean setup, a hybrid approach or any alternative suitable to each company’s or organization’s specific needs. This part is performed in a bullet proof manner when recovery from backup rehearsals have been part of your maintenance process.
- Determine Your Options: You have several ways to deal with the infection. Determine which approach is best for you.
- Report the incident to all stakeholders necessary: Report to all stakeholders including the authorities where necessary. This engages into action everybody to contribute to the preparation of systems and processes to avoid similar incidents.
Cyber security or cyber insurance?
Cyber insurance is an insurance policy that helps protect organizations from fallout from cyberattacks and hacking threats. Cyber insurance claims can be triggered by many sorts of incidents, but right now the most common are ransomware, fund-transfer fraud attacks, and business email compromise scams. Today, internet-based technology is involved in nearly every aspect of life, from healthcare to home security. With that, the top cyber insurance companies have seen dramatic changes in the last two years – Q4 2019 being the tipping point: big players like AXA stop covering ransomware crime[3], or advance at a rapid pace to keep up with ongoing threats[4].
Cybersecurity within the insurance industry is vital because of the industry’s size and scope and the vast amounts of data consumed by companies in this sector. Most likely, Cyber Insurance is not the only solution, at least not on its own. Cyber insurance can be a great way to mitigate the damage caused by a breach, but it should complement cybersecurity best practices as part of an overall cyber risk management plan.
Following up on the latest developments we have been evolving our in-house extended SIEM and monitoring solution, Security Infusion, building a strong tool that supports cybersecurity specialists. For more details of the product, or a security expert’s opinion, feel free to contact us.
[1] National Institute of Standards and Technology (NIST) – Cybersecurity Framework https://www.nist.gov/cyberframework
[2] For more information on ‘’Top Security Priorities’’ that Business Leaders must pay attention, please visit https://www.gartner.com/en
[3] INSURANCE JOURNAL: ‘’Insurer AXA to Stop Paying for Ransomware Crime Payments in France’’, by Frank Bajak, May 9 2021, available at https://www.insurancejournal.com/news/international/2021/05/09/613255.htm
[4] INSURANCE JOURNAL: Ransomware Has Been a ‘Game Changer’ for Cyber Insurance, by Elizabeth Blosfield, August 30 2021, available at https://www.insurancejournal.com/news/national/2021/08/30/628672.htm